Bad IT Habits To Break
Having your day interrupted by IT issues is annoying. It impacts your productivity, which means potentially your clients as well. IT is never going to be foolproof, but there are some questions you can ask yourself to rid yourself of bad tech habits and make your day run a little smoother.
As someone who’s worked on a Service Desk as a tech and Customer Service Manager, I’ve seen some great habits and pretty awful ones! These are the questions I’m asking when common things go wrong, so they don’t happen again.
#1 Are you leaving your PC on?
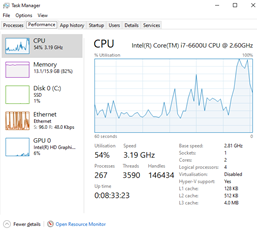
It’s an old cliché, but you might be surprised by just how often ‘turning it off and on again’ really does resolve the issue. PCs are a bit like people: they’re not meant to be on all the time. It can be very tempting to put your PC to sleep so you can start the next day quickly with all your previous days work open and ready to go, with the full intention of turning it off that evening, then rinse and repeat. Before you know it, your PC has been on for a week without a break. Restarting the PC can help speed things up for you; it stops any tasks that might be eating up the memory on your machine, clears out temporary files and gives it a chance to install updates for both software and your operating system. It’s easy to check how long your PCs been on. Just press the ctrl+alt+esc keys together on your keyboard to bring up the Task Manager application. Click ‘More Details’ and then the ‘Performance’ tab, and you’ll see the ‘Up Time’. If it’s more than a couple of days and you’re experiencing issues, it’s always worth a reboot in the first instance.
#2 Are you keeping an eye on space?
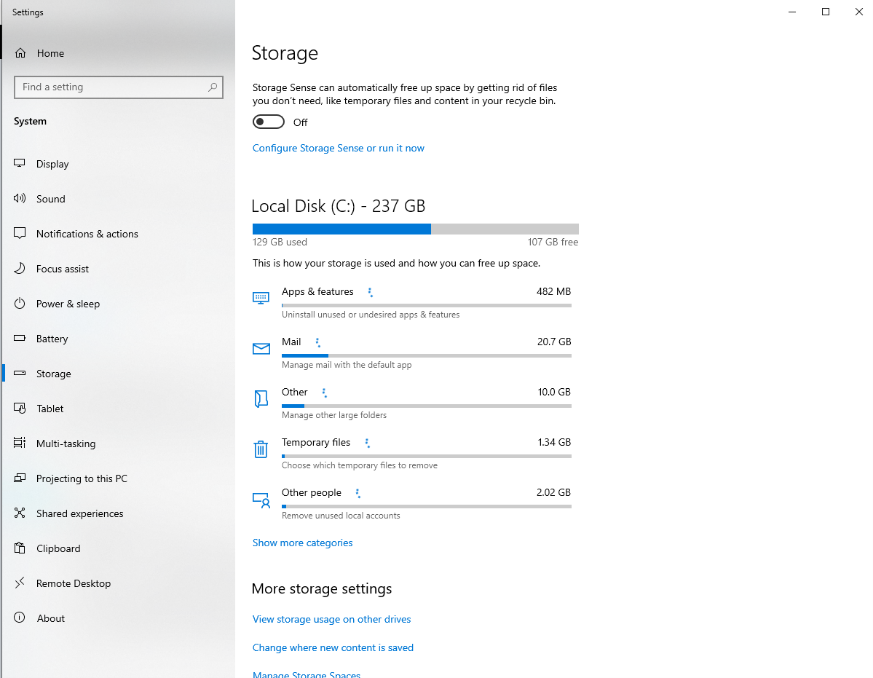
One of the other major culprits for causing PC performance issues is the amount of space you have left on your hard drive. The less space you have, generally, the poorer your PC will perform. Whilst the operating system on your PC will take up unavoidable space, there’s plenty of other places you can keep an eye on for space-saving. If you type ‘Storage’ into the Windows search bar, you can see just what’s taking up all the space:
Temporary files are often an excellent place to start; these can be items sent to your Recycle Bin or items in your download folder which are no longer needed. Otherwise, removing Apps you don’t need or use anymore can also be a great space saver.
#3 Were you expecting that email?
91% of successful data breaches started with a spear-phishing attack. It’s a scary number. Phishing and spear-phishing is the process of sending an email with the aim of getting you to hand over sensitive information without realising, often, your passwords. This can be done by impersonating or ‘spoofing’ an email address or using a breached account to send out emails. For example, you might receive a link to a document that needs you to pop your password in to access, or maybe a PDF to download. The first question to ask is always ‘Am I expecting this from this sender’. If someone’s sent an invoice or a document for you to open, do you usually receive communications like this from that sender? If you’ve clicked the link, does it look like your company sign-in page? Do you typically have to put a password or multi-factor code in to access files? If the answer to these is ‘no’, then you might be at a fake sign-in page designed to store your password for hackers to steal. Questions like these are the first line of defence in avoiding potentially costly breaches to company data.
#4 Do you have support for critical applications?
You’ve got your IT team to help support you with your day-to-day issues with your PC or network. But there will be times when a certain piece of software isn’t playing ball, and your IT support may need specialist help to resolve it. You might feel like paying for specialist support isn’t worth it when you already pay for IT support, but the question to ask is, how much will it cost me if this system goes down for an hour? For a day? Permanently? And how much quicker your IT experts will get it fixed with support from the software specialists. Less downtime for you, more productivity for staff and clients who never know things went pear-shaped!
#5 Do you check what’s on your social media?
In today’s tech-savvy world, it’s nigh on impossible for a company (and its employees) not to have a presence on social media. From people tagging where they work to the company promoting its business and engaging with clients and new business, there’s a wealth of information being broadcast about a company that hasn’t been available in the past. However, from a security perspective, it opens a company up to far more risk; the more information out there, the more a hacker has to work with. This isn’t to say that there aren’t huge benefits to using social media. Still, good IT habits could include creating a social media policy for employees, not posting full names and positions within the company to reduce targeted attacks or enabling multi-factor authentication on accounts linked to your social media.
#6 Are you talking to your IT Team?
You might feel like when you call for IT support; you get hit with 20 questions. We promise we’re just trying to help! The more information we obtain from you initially, the quicker we’ll be able to pinpoint your issue and get you back up and running. There’s a better chance we will get you through to the right person too, who can fix your problem quicker. Whilst your Service Desk will all have a good working knowledge of all things IT, there will always be people who specialise in certain areas. The more we know, the more likely you are to get to them.
Equally, we promise we don’t mind being bothered. It’s what we’re here for after all! We’d much rather you called us about the ominous beeping in the corner of your server room so we can investigate before it becomes a bigger issue and more downtime for you. We’re always happy to help you shake your bad office IT habits!


Investing in specialized support for critical applications ensures prompt resolution of software-related issues, reducing downtime and maximizing productivity. Furthermore, maintaining a secure presence on social media platforms requires implementing policies and security measures to mitigate potential risks associated with online exposure. By incorporating these practices into your daily routine and fostering a culture of proactive IT management, you can minimize risks, optimise performance, and ensure a seamless workflow for your organisation.