Not long ago, phishing was primarily aimed at the consumer market, and malware was considered the biggest threat to businesses. Today, phishing is the top social attack on businesses and responsible for most security breaches.
Education is one of the best ways to prevent your team from falling victim to a phishing attack.
What is phishing?
Phishing attacks are techniques used by cybercriminals to con users/employees into revealing sensitive information or installing malware by way of electronic communication.
Phishing attack methods
Mass-scale Phishing: Attack where fraudsters cast a wide net attack that isn’t highly targeted.
Spear Phishing: Tailored to a specific victim or group of victims using personal details.
Whaling: Specialised type of spear phishing that targets a “big” victim within a company.
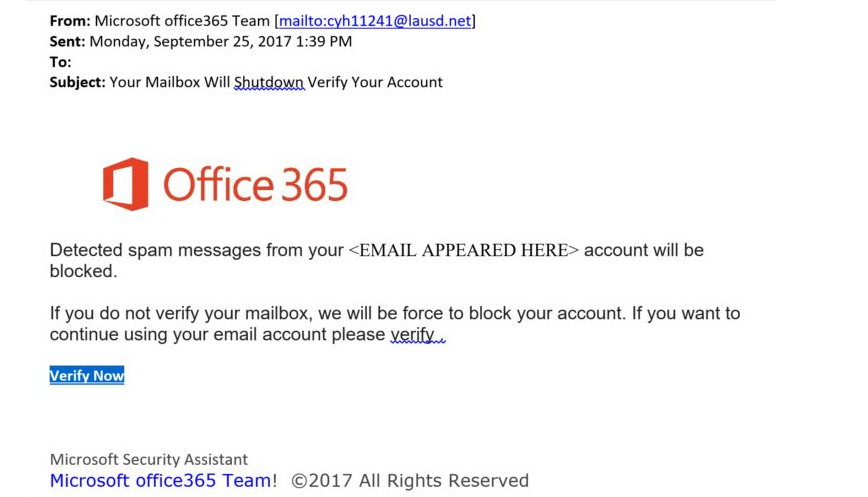
What can you and your staff look out for?
Sender: Have they used a spoof domain address? This allows them to imitate a well-known brand.
Always look at the sender’s name and email address very carefully, look for missing or added letters or symbols. For example, if a phisher was trying to impersonate Microsoft.com, they might use Microsoft.co instead.
Message: An impersonalised message could spell a mass-scale pishing attack.
Unlike mass phishing emails, spearfishing messages are highly personalised and will often reference co-workers or friends name.
Attackers often create a sense of urgency that puts users in a panic mode where they are more likely to fall victim to an attack.
Spelling and grammar can play a big role in the detection of phishing emails. Check for fonts that don’t match the brand, spelling mistakes and grammatical errors.
Attachments: Always be wary of suspicious links and compressed files.
Common file attachments (.doc, .xls, .ppt etc.) can contain malicious macros.
The spoofed link text can hide a hyperlinks actual destination.
Links to spoofed versions of well-known websites can look legitimate and are used to steal information submitted via forms or distribute malware to visitors.
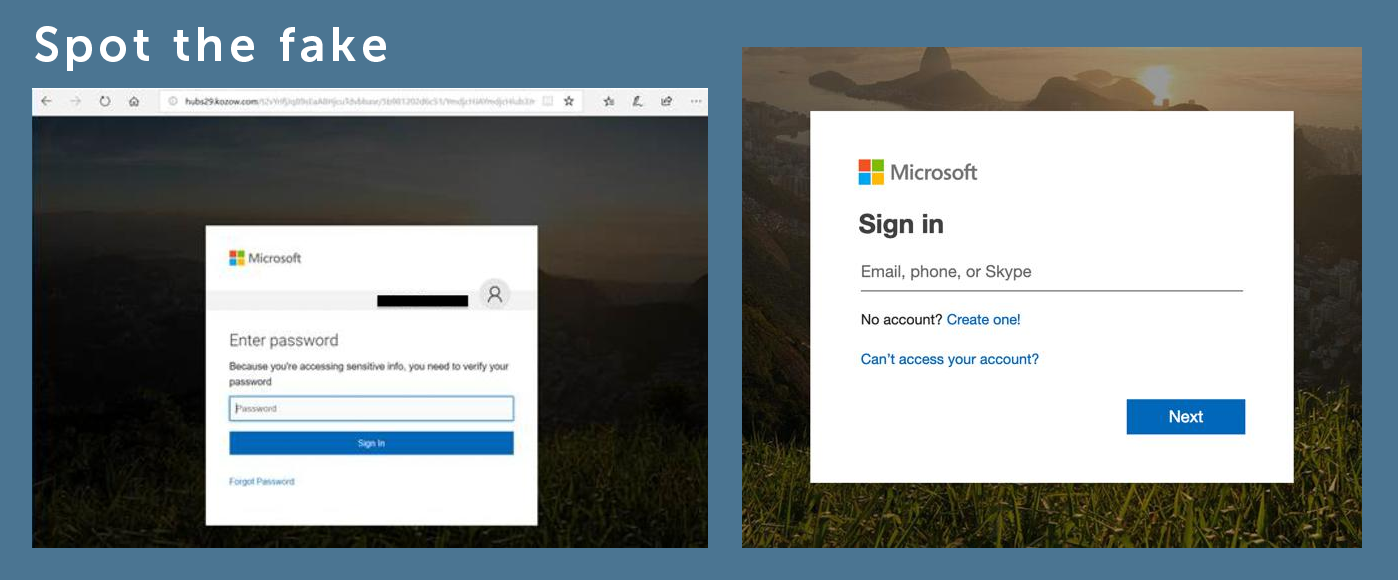
Take measures to protect yourself
Make sure you and your staff keep up to date with the latest phishing scandals, always use anti-virus software and make sure you implement a backup and disaster recovery system for when the worst happens.


In the relentless battle against cyber threats, education is a beacon of resilience, offering a potent defence against the pervasive menace of phishing. As phishing attacks continue to evolve in sophistication and scale, it's imperative for businesses to equip themselves and their staff with the tools needed to discern and thwart these malicious campaigns.
By staying vigilant against tell-tale signs like spoofed domains, personalised messages, and suspicious attachments, organisations can bolster their security posture and safeguard against potential breaches. Moreover, investing in proactive measures such as anti-virus software and robust backup and disaster recovery systems further fortifies defences, ensuring resilience in the face of adversity.
Together, let us champion a culture of cybersecurity awareness and empowerment, where knowledge becomes our most potent shield in the ongoing battle to protect against phishing and other cyber threats.